Secure
messaging

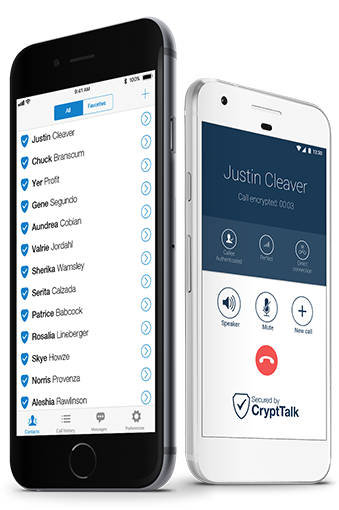
Secure, encrypted messaging
is a standard feature of CryptTalk.
Encrypted
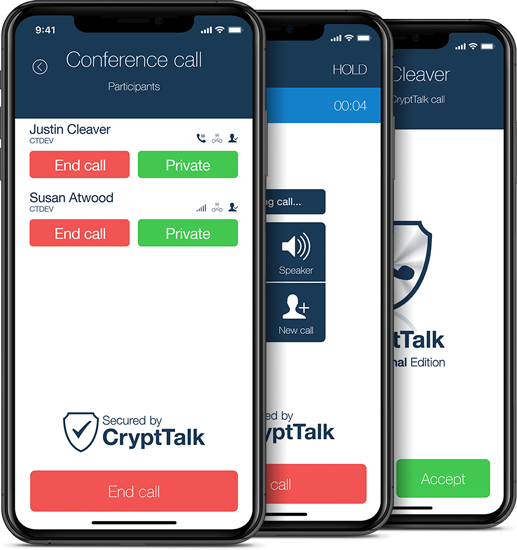
conference calls

CryptTalk features secure conference calling
between multiple CryptTalk users.
Encryption alone is not enough...
...authentication is also critical
Other secure communication services focus on the encryption. They do not verify the identity of the parties.
The authentication used by CryptTalk ensures that the person at the other end of the call is indeed the one you want to communicate with. CryptTalk also protects against man-in-the-middle attacks.
Perfect forward secrecy
CryptTalk's security is ensured by best-practice encryption. We use the Diffie-Hellman method of key exchange to establish a short-term, shared secret encryption key. This is never fully transmitted over the network. Voice and message data is then encrypted using this short-term, shared secret key. Thus even if a CryptTalk user's device is compromised in the future, previously used encryption keys cannot be recovered and all past communications remain secure.
Continuously updated and regularly security-reviewed to protect your privacy.
-
The application was found to be secured to a very good standard and no practically exploitable vulnerabilities were found. Clear evidence was present of proactive security measures, and the product's design is very well thought-out. (NCC Security Assessment (2015 June) - Section 1.4.1)
-
The underpinning cryptographic protocol had been well conceived, and no faults were found within its implementation. (NCC Security Assessment (2015 June) - Section 1.5, para 1)
-
It was confirmed that an attacker with no knowledge of the user's PIN is not able to gain access to any sensitive information, either by intercepting traffic or analysing data held on the device's storage.
(NCC Security Assessment (2015 June) - Section 1.5, para 3)
List of features
Security
Features
- Comprehensive, secure call and instant message features with military grade encryption and authentication
- End-to-end encrypted calls with asymmetric keys and digital signature protection:
- Calls are not transmitted through a central server
- Keys are generated on the fly on the user's devices are destroyed after every call and are not stored anywhere
- Built on the most secure algorithms which are recommended by prominent IT security experts and trusted by military services worldwide
- No backdoors: the communication cannot be deciphered even if the interceptor has the source code of the application or administrator access to the central servers
- Contact management with strong security - identity management with certificate handling
- Only necessary information is stored with strong protection of stored data
- No local authentication on the device - all authentication happens with the central authentication service
- Strictly guarded and monitored operation centers with several back-up locations and secret stand-by sites if disaster recovery is needed
- Servers used by the service can be deployed within an isolated corporate environment where it is impossible for the vendor or unwelcome third parties to gain access
- Secure user management features: all user management-related processes and procedures are secured in line with the highest safety standards
Network and
Coverage
- Worldwide service coverage - subscribers with proper internet access can use our services anywhere on the globe
- Requires only a generic IP network - Supported internet environments:
- Comprehensive independence from service providers, carriers, or networks
- Encryption cannot be perceived by the network service provider
- Automatic handover when switching between networks during active calls
Comfort Features
- Easy to use: provides high security yet remains easy to operate without changing the way you already communicate
- Superior voice quality, shortest delay
- Support of Mobile Device Management (MDM) systems
- Multitasking and push notification support
- Presence handling
- Do Not Disturb (DND) mode
- Support of multiple languages (EN, SE, CN, BR, HU, KOR)
- Call history with security features
- Setting of notification sounds and ringtones
- Bluetooth device support
- Call quality indicator
- Support of proximity sensor
- Handling of interruption of active CryptTalk calls by GSM calls
- Easy installation and activation
- Support services and SLA
Contact and
User Management
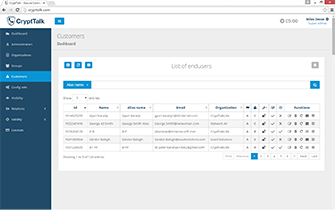
- Professional user management and administration interface for system administrators and managers:
- Application-level user management features for end users to keep their contacts easily organized
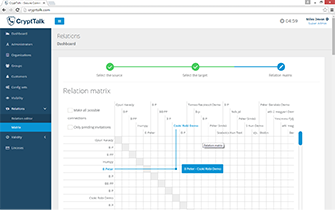
- Professional administration interface designed for system administrators and managers of your organization to manage user relations and visibility, moreover connections with other companies and other organizations using CryptTalk
Other Features
- Flat-rate, secure communication service: the monthly service fee includes unlimited free worldwide secure calls and instant messaging over Wi-Fi and mobile internet networks without additional per-minute or per-message costs
- Available as Software as a Service (SaaS):
- No long-term commitment or investment needed
- Customers pay a license (subscription) fee
- Available as an isolated hosted service or can be deployed with on-site company infrastructure
- Support of multiple platforms (iOS, Android)
- Customization of the application is possible upon request
- Legal solution to protect private and business communication
Designed to meet advanced business requirements

Enterprise features

Swedish vendor

Best value
Professional admin interface
and user management
System administrators will find CryptTalk's business solutions easy to configure and maintain.
The user management interface allows adding CryptTalk users from outside the enterprise in a trusted yet secure manner.
All user management procedures can be made compliant to match the strictest internal company policies.
Hosted service or
on-site deployment
By default, the CryptTalk service is hosted by Arenim Technologies AB. However, should your IT or security policy require it, the CryptTalk backend can be installed in a dedicated private cloud or in your company's internal network.
Best-Practice Cryptography & Comprehensive Protection
Media encryption

AES-256 in CTR mode
max. block cipher protection
Authentication

One Time Password (RFC 4226)
with SIP Digest
Key exchange

Elliptic Curve Diffie-Hellman
with ephemeral keys signed using RSA-2048,
end-to-end key exchange
Private key protection

Patented, proprietary method for top security
(see White Paper for details)
Man-in-the-Middle Protection

Diffie-Hellman key exchange messages
signed using RSA-2048
Integrity protection

Signed
Voice / IM packets
SRTP authentication

HMAC-SHA1
RTP control data protection

Secure RTCP
Replay Attack Protection

Key exchange with challenge-response

Jailbreak / Rooting detection
Spyware protection

P2P conference calling
without mixing server

Perfect Forward Secrecy
Guard against eavesdroppers
with the world's most reliable secure calling service.